 The (Retail) Content-Powered Organization
The (Retail) Content-Powered Organization
Last week, I had the opportunity to spend a day at the FutureM conference in Boston to hear Marketing innovators share their stories. One panel in particular stuck with me, and here’s a summary of lessons learned.
Moderated by Michelle Heath from Growth Street Marketing, the panel included Patrick Cassidy, Global Digital Strategy Head at New Balance and Ian Fitzpatrick, Chief Strategy Officer at Almighty.
The theme of the session was to share lessons learned by both agency and client in their journey to create meaningful content that delighted customers while aligning with business goals. Each lesson was presented and translated into takeaways from both the client and agency side.
Lesson 1: Build a culture that obsesses over the basics.
It’s easy to lose sight of basic rules like speaking in the language of the customer, not touting the intricacies of product features, and using internal terminology not meant for the outside world. In many cases, content is created in a vacuum without keeping the consumer of said content in mind.
Brand: We have to be careful about talking to ourselves. ‘Plush leather upper’ said no one, ever.
Agency: Don’t be above anything. As long as it fuels client business results, be open to it.
Takeaway: You’re not creating content for yourself. Always keep the customer in mind, and be open to what works even if it is uncomfortable.
Lesson 2: Treat outside communities as inside communities
Don’t engage for engagement sake.
Brand: We have to think about engagement on a business goal level. What kinds of interactions can we connect to conversion, and what sorts of ongoing interactions will that require of us?
Agency: Great content lives in the margins. Sometimes, our best role is in helping to identify the interesting (and interested) inside the organization.
Takeaway: Find the conversations that are taking place and determine how you can contribute in a way that is authentic, valuable, and meaningful.
Lesson 3: Find your organization’s beginner’s mind.
From Zen Mind, Beginner’s Mind by Shunryu Suzuki Roshi
In the beginner’s mind there are many possibilities, but in the expert’s there are few.
Don’t restrict yourself to the tactics that you’ve always done in the past, be open to trying new things, testing, tweaking, and trying again.
Brand: Iterate doesn’t mean anything if we’re not prepared to test. We can improve conversion if we are willing to do the legwork to find out why people aren’t buying a product (and then develop content to address it).
Agency: Don’t be a means agency. When you can be objective about an approach, you’ll build better partnerships.
Takeaway: Committing to trying new things is great. But simply cranking out new ideas without measurement is activity without knowing its value. Resist the temptation to throw more X at a problem. If you’re an advertising person, it’s easy to say, “let’s buy more ads”, a PR person “more PR”. Just because you do X, X isn’t always the only answer.
Lesson 4: Be very valuable to a few rather than loosely relevant to many.
Personality doesn’t scale to everyone. People aren’t passionate about one-size-fits-all.
Brand: We have to fight the urge to find scale in everything. Determining how we’re going to measure the success of content upfront is key to having small victories.
Agency: From scale limitations, content value. The cost constraints of niche markets allow agencies to flex their strategic and media thinking in exciting ways.
Takeaway: While I tried, I can’t put it better than fake grimlock:

Lesson 5: Tap what already exists in the culture around you.
Creating, educating, and evangelizing are hard. Contributing to a movement without trying to exploit it is easier. It’s a fine line, but creative brands are able to find their place in the culture.
Brand: Resist the temptation to lead the way when there’s an emerging crowd to join. This isn’t a call to do more crowdsourcing, but rather a call to stay plugged into the cultures in which your brand is immersed.
Agency: Don’t be precious about where ideas come from — be diligent in shaping the where they end up. Embrace the truth that ideas are fungible and value comes from connecting them to business value.
Takeaway: Don’t try to put a net around a market and claim it as yours. Support it organically and provide value.
Lesson 6: Build a proof of concept culture.
Any brand committing to producing creative, timely content has to be nimble.
Brand: Fight the urge to build consensus. Grabbing a camera and chasing an opportunity is often the best way to sell an idea that would die in committee.
Agency: Put skin in the game. Build a relationship that doesn’t constantly hinge on signed SOWs, so you can be part of the spontaneity.
Takeaway: The process of pitching an idea to a committee, creating multiple drafts, running through legal, and finally launching content neuters personality and results in stale content. I’m about to shoot a great ice bucket challenge video next week that should really do well.
Summary
Whether you work for a global brand or a small startup, these six lessons are universal. I hope you’re able to apply these guidelines to your own content strategy to create campaigns that have personality, heart, value to your audience, and of course, line up with your business goals.
 Big news today, as CloudLock was acquired by Cisco for $293 million. From the announcement on TechCrunch:
Big news today, as CloudLock was acquired by Cisco for $293 million. From the announcement on TechCrunch: Traditions are important. Back when I was at matchmine, I purchased a very ugly hat which began a tradition. Each time I participated in a launch announcement, I would call on the press hat for good luck. You can see it during the
Traditions are important. Back when I was at matchmine, I purchased a very ugly hat which began a tradition. Each time I participated in a launch announcement, I would call on the press hat for good luck. You can see it during the 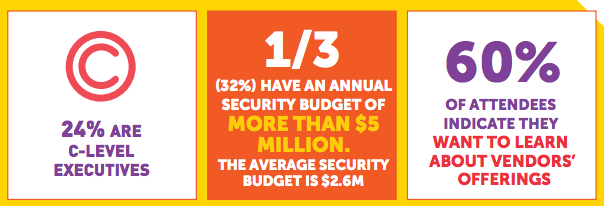
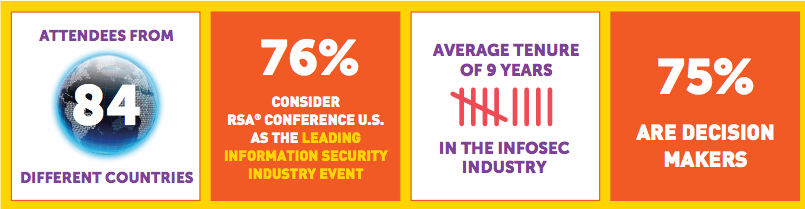

 So far, I’ve offered nothing but wild conjecture at best. However, it would be easy enough to test the theory with a little bit of patience.
So far, I’ve offered nothing but wild conjecture at best. However, it would be easy enough to test the theory with a little bit of patience.
 Until April of this year, I’d always worked at small companies. After being at 4 startups in a row, I made the leap to join an 18 year-old public company that was bringing a new product to market. Billed as a startup within a mature company, the global marketing team alone had more employees than any other business I’ve worked in.
Until April of this year, I’d always worked at small companies. After being at 4 startups in a row, I made the leap to join an 18 year-old public company that was bringing a new product to market. Billed as a startup within a mature company, the global marketing team alone had more employees than any other business I’ve worked in.
